Main Concepts¶
...
Testerman is a project that brings most of the powerful capabilities and concepts of TTCN-3 to the Python programming language, both providing a set of Python libraries and a complete, multi-user, distributed test execution environment.
TTCN-3 is a test description language standardized by the ETSI as ES 201 873. Testerman implements most language primitives described in its part 1 (ES201-873-1: TTCN-3 Core Part) as Python functions, however it drops all the strict typing model of TTCN-3 and privileges the weak typing of Python, enabling to write test cases faster than in TTCN-3.
Testerman is not meant to replace or to compete with such a growing supported standard. Instead, it tries to fill the gap between the existing, closed-source, expensive TTCN-3 tools on the market and the other testing tools that are dedicated to one family of protocols, forcing the users to develop glues to synchronize them together, and create additional scripts to test non-protocol things such as log files, database updates, etc.
By using the same concepts as in TTCN-3, your time investment in Testerman can be fully reusable when migrating to the standard, if needed: the test logic implementation, objects and primitives remain the same, only the syntax changes.
Testerman has been designed to be multi-user (client-server) with a centralized test cases repository, adaptable to most SUT topologies and network constraints (distributed test/system adapters), and extensible (test/system adapters can be developed easily, in any language).
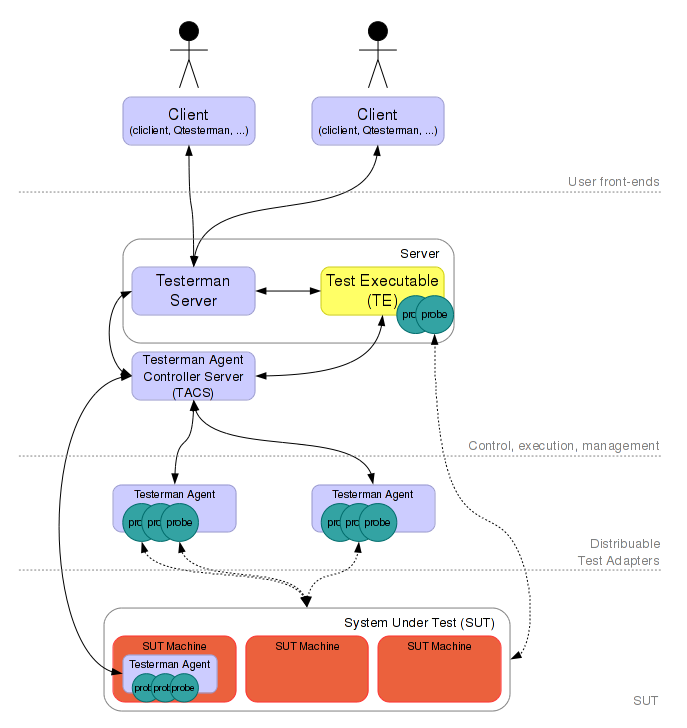
Users interact with the system through a Testerman client. Any number of clients can connect to the same server, enabling to share the same ATS repository and the same technical resources (the agents, see below). Currently, the following clients are available:
CLI and rich client should be installed on the user’s workstation. However, developing a full fledged web-based client (with test designs and writing capabilities) is quite possible.
The server is actually split into two components:
They are the result of a “compilation” of the ATS into something runnable by the operating system. In a real TTCN-3 execution system, the ATS, written in TTCN-3, would probably be transformed into Java or C++ code before being compiled with a standard compiler, and linked to specific libraries according to the tool vendor. These libraries then enable the TE to access a Platform Adapter (PA) and System Adapters (SA) modules that implement actual, technical services such as timers, message encoders/decoders, and connections to the SUT (actual socket management, writing and reading on the wire, etc).
In Testerman, the ATS, writing by the user in Python and calling Testerman-provided functions, is also transformed into a special Python program that embeds additional Testerman modules (the Python word for “libraries”) to provide an access to the Testerman environment functions. In particular, these libraries enable the TE to access the probes either hosted on a distant agent (“remote probes”) or run from the same location as the TE (“local probes”).
A probe is the Testerman word for the implementation of what TTCN-3 would call a Test Adapter (aka a System Adapter). This is the piece of software that can actually connects to a SUT (System Under Test) using different protocols (such as tcp, udp, sctp, or higher level ones: http, rtsp, Oracle, SOAP, XMLRPC, ...).
Testerman provides a collection of probes to be able to interact with
the SUT using most usual protocols but also to interact with it
simulating user actions or anything needed to automate a test you can do
manually. For instance, the probe whose type is watcher.file is able
to monitor any (text) file on a system, and sends notifications when a
new line matching some patterns was written to it. Some others enable
you to simulate command line commands, as if you were opening a local
shell on the machine and running some commands locally.
Probes can be run by the TE itself, running on the Testerman Server and thus initiating or expecting network connections on the Testerman Server’s IP interfaces (which may not be possible in all SUT topologies), or can be run on any distant system. In this case, they need to be hosted on a Testerman Agent, responsible for managing the low-level communications with the Testerman Agent Controller Server (TACS).
Agents must be deployed (i.e. installed and started) manually by the tester. However, once deployed, an agent may be used by any TE to deploy (dynamically) any number of probes on it, according to its defined Test Adapter Configuration.
This Agent-oriented architecture enables to distribute probes anywhere in the network, either around the SUT or inside the SUT itself. This provides several benefits:
For now, the main (and single) Testerman agent implementation available is written in Python (that’s why it is dubbed PyAgent) and can host any probes that can also be run locally by the TE, sharing the same plugin interface. This PyAgent can also be updated remotely from the TACS+Testerman Server, making Testerman administrator’s and user’s lives easier when new updates are available.
...